- Governance of information technology based on the requirements of DORA.
- Governance of information and cyber security.
- Implementation of IT and information security in line with DORA.
- Hands-on assistance in the development of the Digital Operational Resilience Strategy.
- Organizational discussion related to both the first and second lines of defense within ICT, including responsibilities and mandates.
- Tailoring of ICT risk management frameworks to strategic and regulatory requirements, including business needs.
- Integration of the ICT risk management framework with the overall risk framework, including alignment of risk appetites, limits, and Key Risk Indicators.
- Assisting with the reporting framework to executive management, the Board of Directors, and competent authorities.
- Assisting with Board of Directors training and education.
Enhancing Digital Operational Resilience with DORA
The DORA legislation, introduced by the European Commission to ensure digital operational resilience in the financial sector, has been adopted and is currently in the implementation phase.
To comply with DORA, most financial institutions will need to make adjustments. Our services can assist you in identifying the necessary steps and implementing the required changes to maintain compliance.
We help you navigate DORA effectively by delivering regulatory updates, analysis, and actionable insights.
DORA Defined
The Digital Operational Resilience Act (DORA) within the Digital Finance Package (DFP) unifies ICT risk and outsourcing regulations across the EU. Published in Official Journal of the EU in December 2022, DORA promotes the growth of digital finance while addressing risks, applicable to a wide range of financial entities and critical third-party ICT service providers.
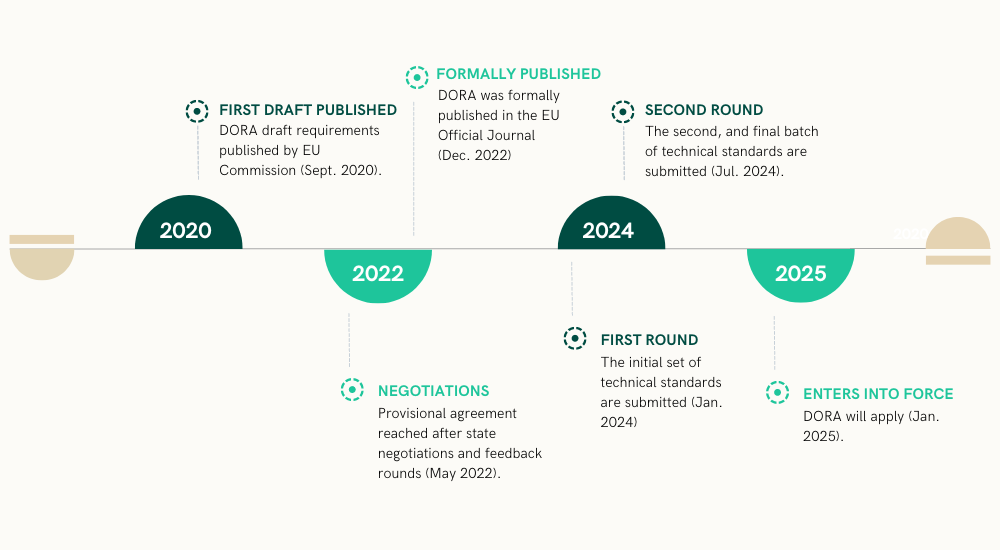
DORA Explained

First Batch of DORA Technical Standards Open for Public Consultation
The European Supervisory Authorities (EBA, EIOPA, and ESMA – the ESAs) have released the first batch of DORA’s technical standards.
Insights & Implications

Vulnerability & Threat Management
Vulnerability and threat assessments are fundamental parts of DORA. Explore the key components and success factors.

Digital Operational Resilience vs BCM
A well-functioning BCM can not be interchanged with having achieved digital operational resilience.

Future Roles of CTO & CIO
CTOs and CIOs are experiencing an increased workload as ICT and security risk is one of the areas receiving most attention.

Holistic Multi-Vendor Strategy
Designing a holistic ICT multi-vendor strategy is a complex process, requiring a high level of knowledge and competence.

Enhance the Digital Operational Resilience in Your Organization
Our DORA Services
Strategy, Governance & Organisation
Information & Cyber Security Management
• Development of a state-of-the-art Information Security Management System (ISMS), tailored to your risks, exposure, size, and complexity.
• Hands-on experience with processes, routines, and internal controls to implement the ISMS.
• Experience in integrating the ICT risk management system with the ISMS.
• Data scientists and mathematicians available to assist you in developing models to measure risk exposure and maturity in both information and cyber security.
• Deep insight and best practices derived from numerous supervisory processes and an in-depth understanding of regulatory requirements, allowing us to tailor our recommendations to meet your needs.
• An experienced and dedicated cyber security team that provides hands-on assistance in identifying, protecting, detecting, responding, and recovering from cyber security incidents, including cyber security architecture.
• CISO-as-a-Service.
Incident Management
• Practical interpretation and tailored incident management processes adapted to all applicable regulations and aligned with internal processes and routines in your company.
• Develop an incident classification scheme adapted to your needs and in accordance with applicable regulations.
• Governance, routine, and reporting templates and routines to facilitate smooth reporting to regulatory authorities.
Testing
• Governance, processes, and routines to perform an adequate information and cyber security testing program (testing framework).
• Assist you in developing the testing capabilities needed to support the testing program, including vulnerability assessments, external intelligence, network security testing, gap analysis, source code reviews, compatibility and performance testing, and penetration testing.
• Assistance and delivery of Threat Lead Penetration Testing (TLPT).
Operational Resilience
• Assistance in developing an operational resilience strategy that is aligned with your visions, values, and goals, and where the strategy is sufficiently concrete to manage and anticipate any potential future disruptions.
• Align the operational resilience strategy with your risk management framework and exposures.
• Support the development of your operational resilience with hands-on experience, best practices, and alignment with regulations.
• Assistance in developing testing plans and innovative testing exercises for your operational resilience ability.
• Resilience testing as-a-Service.
Management of Third-Party Contracts & Risks
• Information and cyber security experience in outsourcing or third-party vendor management, encompassing the pre-phase, contract phase, and ongoing monitoring phase of a third-party contract lifecycle.
• Assistance in developing a multi-vendor strategy that aligns with your overall business and ICT strategy.
• Assistance in defining the overall governance arrangements for third-party management, including determining if the arrangements involve outsourcing or services and whether they should be considered critical or important.
Cyber & Digital Risk
Advisense provides a comprehensive suite of Cyber & Digital Risk services tailored to your unique requirements and needs, serving clients across various business sectors.
Risk & Finance
Advisense provides services to banks, FinTech, insurance companies and investments firms within strategy, governance, internal control, and organisational issues in ICT.








